Table of Contents
Create evaluator with restrictions on one entity
Define evaluator with restriction for one identity (user)
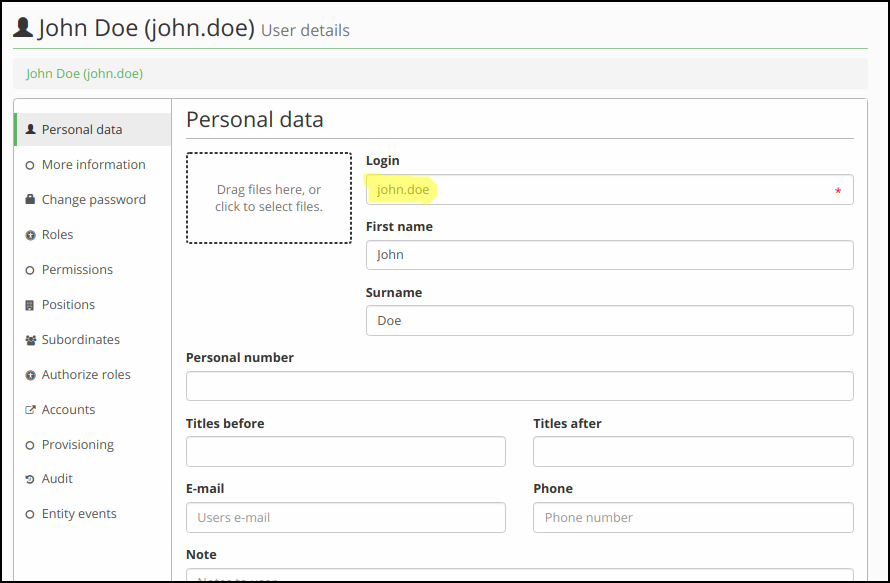
This section describes how to create evaluator that restricts permission to see only one identity (user).
Step 1. - Get username of user
Step 2. - Create codeable evaluator for role
For this step a role must exist so we can hook a new evaluator to this role. If you don't have such a role, please create one. Once you have a role, go to its submenu Permission and then add new evaluator by button Add.
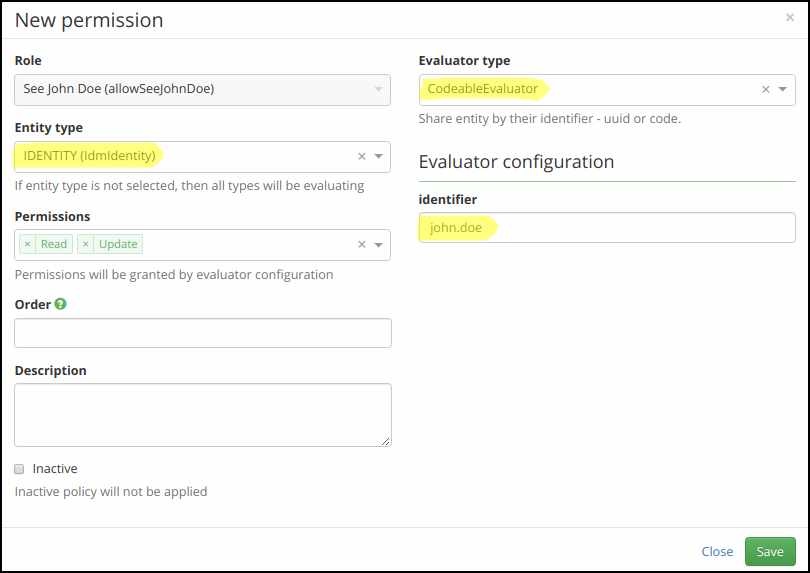
Step 3. - Define new evaluator
On a modal window, select:
- Entity type: IdmIdentity.
- Evaluator type: CodeableEvaluator
Then, application will display an evaluator configuration dialog with one option marked identifier. Put UUID or username of an user (identiti) into this field.
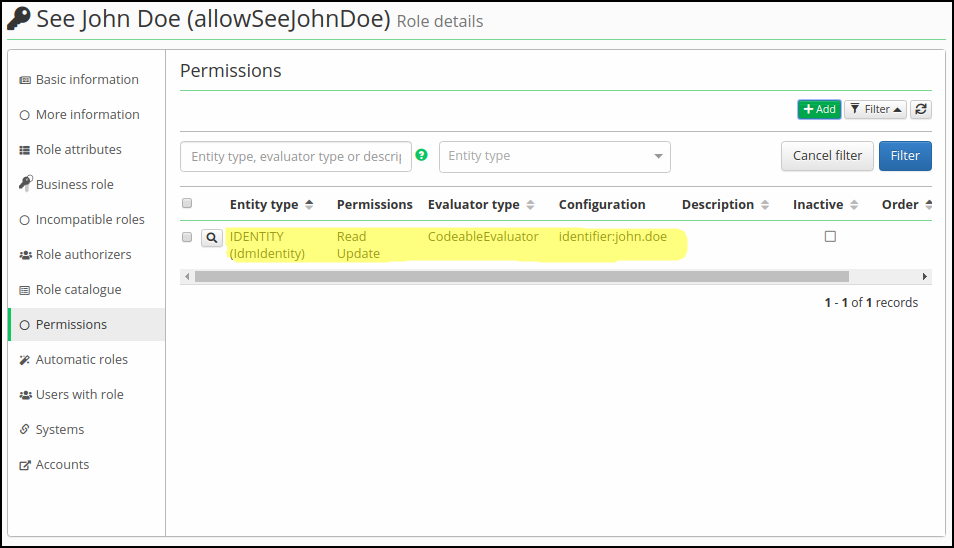
Save the new evaluator. If the action was successful, you can verify new evaluator in the list of active evaluators.
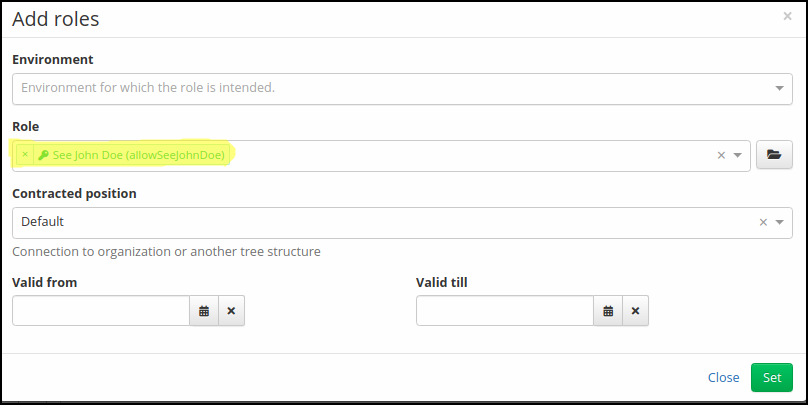
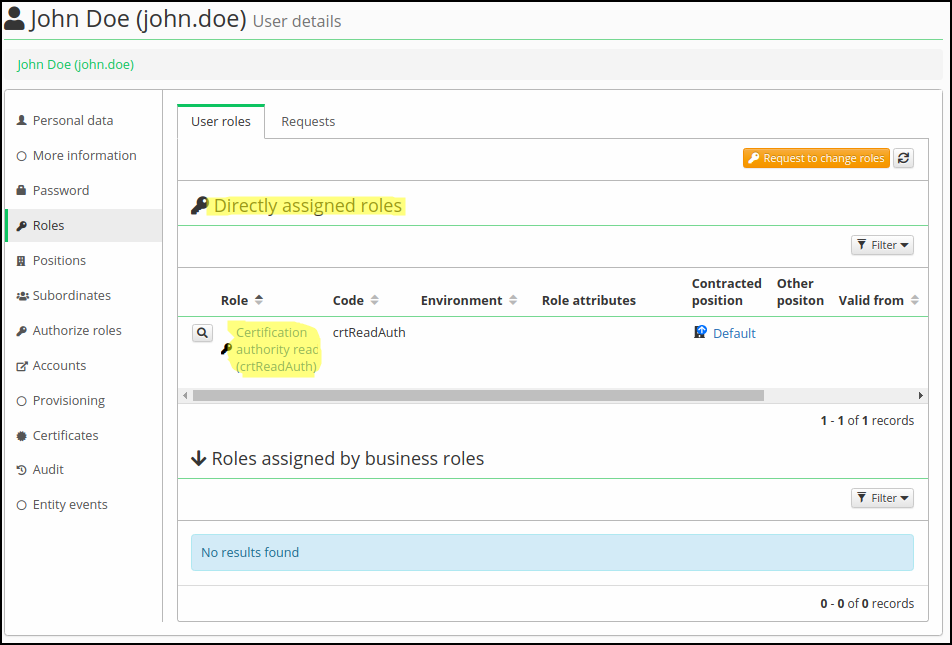
Step 4. - Add role to user
Choose some other user (the user you want to give the permission to) and add him the role you configured. This user now obtains a new permission as defined in the evaluator.
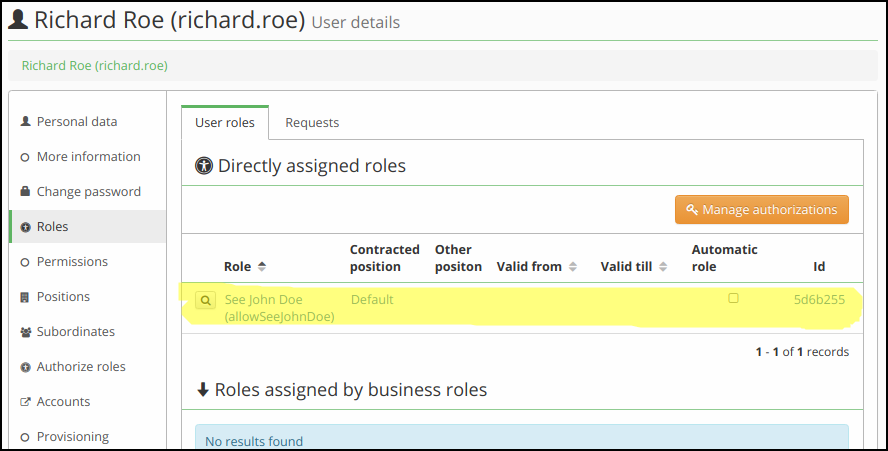
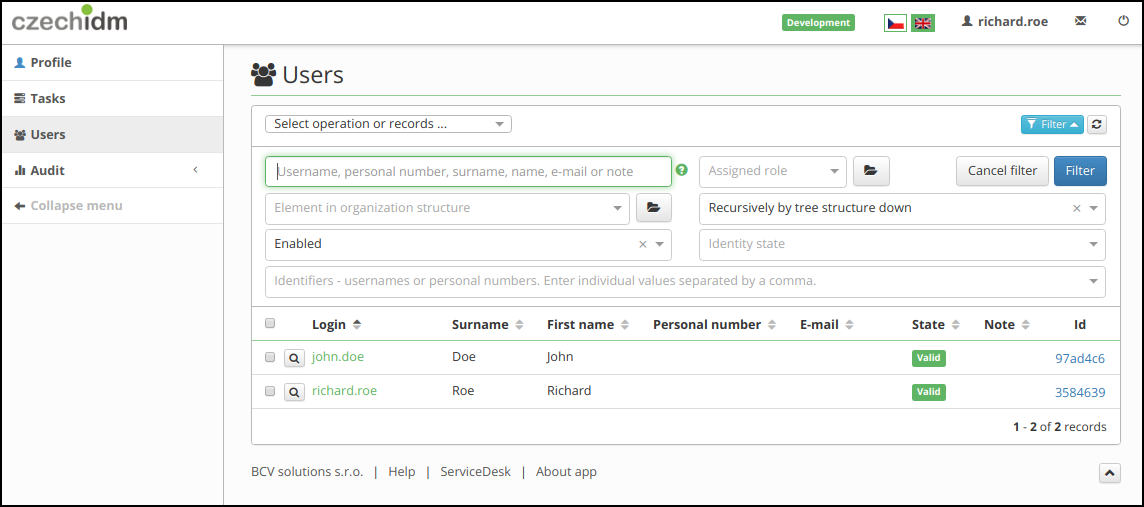
Step 5. - Result
Final result. We assigned a role to the richard.roe. This user now can see the john.doe identity in IdM.
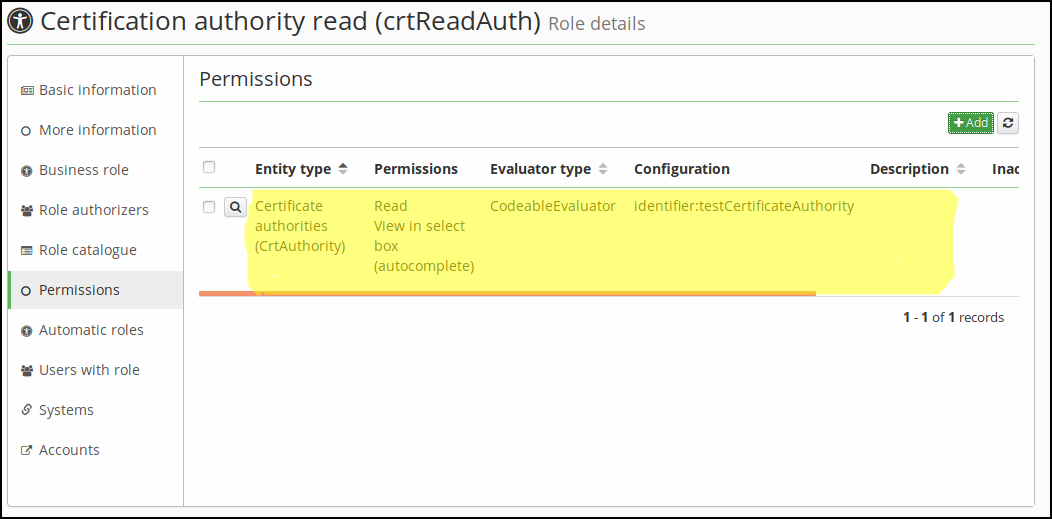
Define evaluator with restriction for access to one certification authority
This tutorial is similar to the first one. Instead of an identity, we grant user a permission to work with some certificate authority. For example, this restriction can be used for adding permissions to request certificates only from particular certificate authority authority. If you have multiple CAs defined, you can create one role for each of your CAs an then assign those roles to users as necessary.
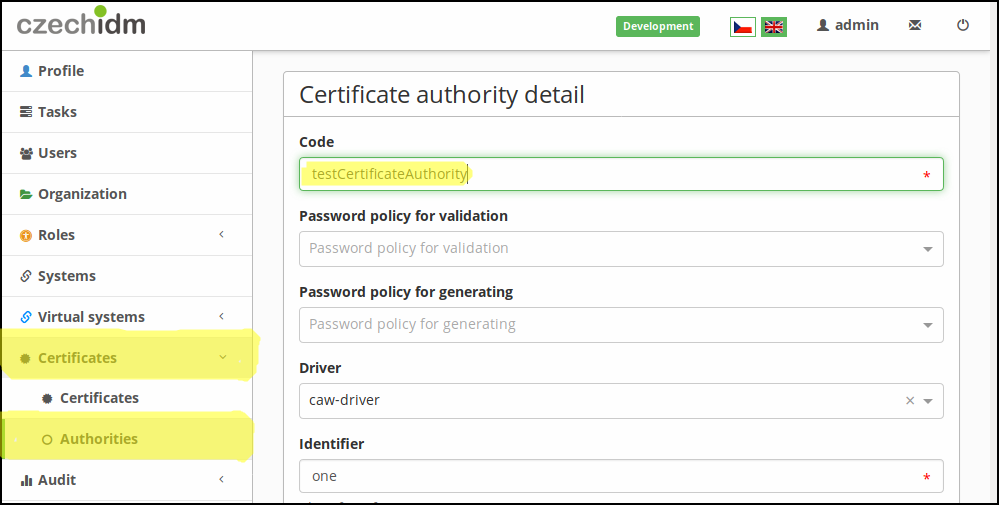
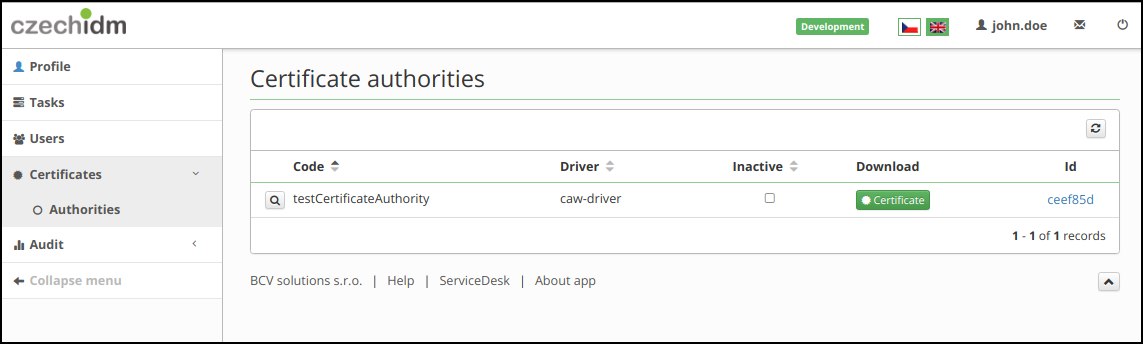
Step 1. - Get code of certification authority
Get the code of certification authority.
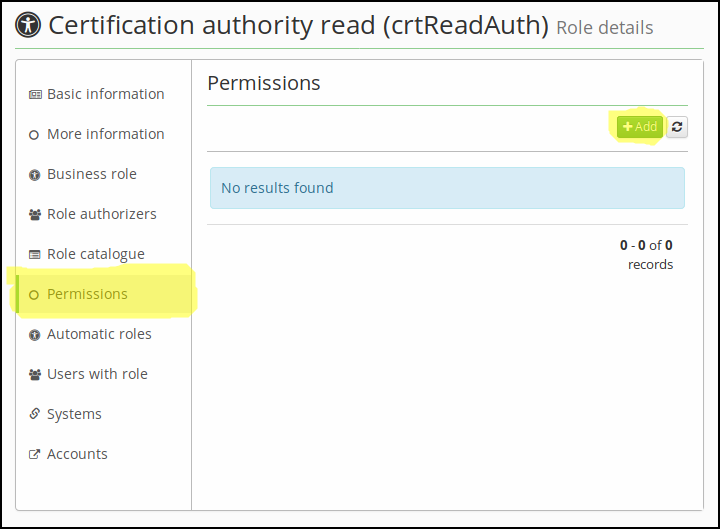
Step 2. - Create codeable evaluator for role
For this step you have to have a role created (if you do not have such a role, create it). We will now hook an evaluator to the role. For this, go to role's submenu Permission and then add new evaluator by clicking the Add button.
Step 3. - Define new evaluator
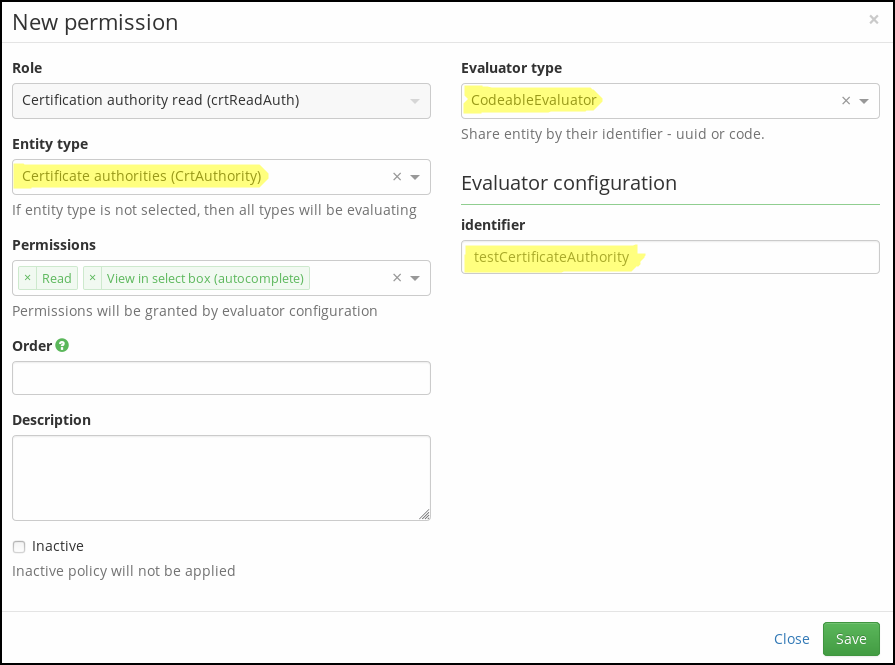
On modal window, select:
- Entity type: CrtAuthority.
- Evaluator type: CodeableEvaluator.
Application will display an evaluator configuration dialog with one option marked identifier. Fill in the identificator of certificate authority.
Save new evaluator. If everything is ok, you can see it in the list of existing evaluators.
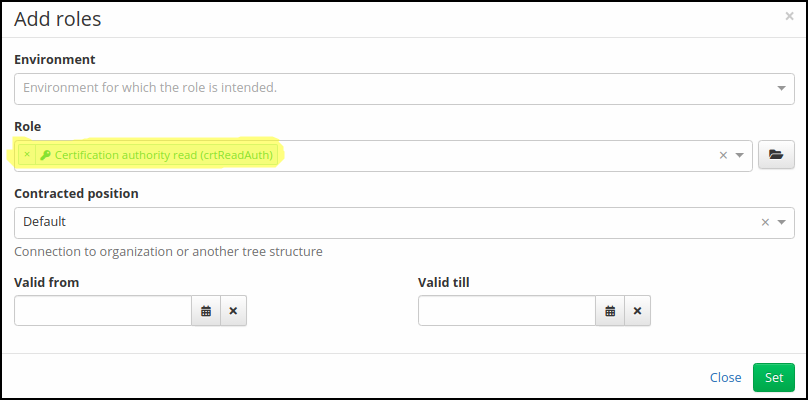
Step 4. - Add role to user
Add a role to some user. This user will now obtain a permission to work with particular certificate authority (determined by CA identification in the evaluator).