Table of Contents
Remote connector server
Remote connector server is a standalone daemon used for interfacing some of the more difficult systems. You deploy connector bundles into the connector server. Then, you configure CzechIdM to use connectors from within the remote connector server. As far as IdM is concerned, there is no difference if actions on end system are performed by connector server or IdM itself. The only difference is in the point of origin of network communication.
Why use remote connector server?
CzechIdM comes bundled only with certain types of connectors. For some deployments, it is necessary to use Remote connector server ("connector server" from now on). There are generally four reasons for this:
- We cannot run Java code on the target system (e. g. .NET code is needed).
- The OS does not have some normal API (e. g. old Windows without WinRM) so we need to run commands on it locally.
- Security reasons - we do not want to run the connector code under the same user as the CzechIdM.
- You need to use two different versions of one connector (or two connectors which bundle different versions of the same library - for example Apache CXF). If you did deploy them both into one Java context, libraries would break due to Java Class FQDN conflicts.
How does a remote connector server work in CzechIdM?
The remote server connector configuration form behaves just like the local connector form - this means that definition is stored in the EAV attributes for system which it belongs to. System name, connector name and connector version are the key to EAV attributes in the CzechIdM. It is therefore possible to have multiple connectors with different versions in one remote connector server.
Connector server setup
Obtaining connector server
- Simply download the all-in-one prepared bundle from there.
- Download connector server from the ConnId project.
- Use version 1.4.5.1 of remote connector server and version 1.4.3.0 of connector framework.
- Download following libraries and add them to the
libdirectory of the connector server:- jackson-annotations-2.9.8
- jackson-core-2.9.8
- jackson-databind-2.9.8
- Add those libraries to the
classpathinsideConnectorServer.shscript (for Linux) orConnectorServer.batscript (for Windows).
Remote connector server configuration - Linux
- Install Java 1.8 (OpenJDK headless is preferred).
- Create new OS user the connector server will run under. By default, we create user
connector-serverwith home under/opt. <code>
useradd -b /opt -m -s /bin/bash connector-server chmod 750 /opt/connector-server/
</code>
- Copy over the connector server and unpack it.
cp connector-server-master.tar.gz /opt/connector-server/ chown connector-server:connector-server /opt/connector-server/connector-server-master.tar.gz su - connector-server cd /opt/connector-server tar xzf connector-server-master.tar.gz rm connector-server-master.tar.gz
- Correct directory permissions:
cd /opt/connector-server/connid-connector-server chmod 750 bin/ bundles/ certs/ conf/ lib/ logs/ scripts/
- Your setup should look like this:
ls -l /opt/connector-server/ total 4 drwxrwxr-x 9 connector-server connector-server 4096 Oct 10 16:45 connid-connector-server ls -l /opt/connector-server/connid-connector-server/ total 23448 drwxr-x--- 5 connector-server connector-server 4096 Mar 10 10:09 bin drwxr-x--- 2 connector-server connector-server 4096 Oct 18 09:08 bundles drwxr-x--- 2 connector-server connector-server 4096 Mar 10 10:14 certs drwxr-x--- 2 connector-server connector-server 4096 Mar 10 10:04 conf -rw-rw-r-- 1 connector-server connector-server 11976830 Oct 10 16:45 datetime drwxr-x--- 3 connector-server connector-server 4096 Oct 10 16:45 lib -rw-rw-r-- 1 connector-server connector-server 19982 Oct 10 16:45 LICENSE drwxr-x--- 2 connector-server connector-server 4096 Mar 10 11:02 logs drwxr-x--- 3 connector-server connector-server 4096 Mar 10 09:50 scripts -rw-rw-r-- 1 connector-server connector-server 11976825 Oct 10 16:45 sys
- Set executable permission on the main script.
cd connid-connector-server chmod +x bin/ConnectorServer.sh
- Create strong password for the connector server (use
pwgen -1 16or something similar).
./bin/ConnectorServer.sh -setKey -key PASSWORD_HERE -properties conf/connectorserver.properties
- If you plan to connect to remote connector server remotely (not locally on
localhost), edit theconf/connectorserver.propertiesand set/comment out theconnectorserver.ifaddress. - As root, create systemd unit
/etc/systemd/system/connector-server.service:
- connector-server.service
[Unit] Description=Java Connector Server Service After=network-online.target [Service] User=connector-server WorkingDirectory=/opt/connector-server/connid-connector-server ExecStart=/bin/bash /opt/connector-server/connid-connector-server/bin/ConnectorServer.sh -run -properties /opt/connector-server/connid-connector-server/conf/connectorserver.properties SuccessExitStatus=143 [Install] WantedBy=multi-user.target
- Reload systemd, start and enable the connector server.
systemctl daemon-reload systemctl start connector-server systemctl enable connector-server
- For additional configuration, see
conf/connectorserver.propertiesandconf/logging.propertiesfiles. - Connector server is now configured. You can deploy connector bundles into it. You have to restart the connector server for changes to take effect.
- Add connector bundles (
.jars) into thebundlesdirectory. - Add custom scripts the CzechIdM will use under the
scriptsdirectory. - Add certificates to be used under
certdirectory. CzechIdM scripts by default look there.
Configuring log rotation
The principle of rotating logs on Linux is the same as for the CzechIdM. Just create a proper logrotate file /etc/logrotate.d/connector-server:
/opt/connector-server/connid-connector-server/logs/connectorserver*.log {
rotate 90
daily
dateext
copytruncate
missingok
notifempty
compress
}
Configuring SSL truststore
When you interface end systems remotely, you have to secure the communication with TLS. For this to work, you need a Java truststore. This short howto will show you how to create one.
- Get (or create - as we do there) a certificate of the end system.
su - connector-server cd /opt/connector-server/connid-connector-server/conf openssl genrsa -out fakecert.key openssl req -new -key fakecert.key -out fakecert.csr -subj "/C=CZ/ST=Czech Republic/L=Prague/O=BCV/CN=Connector placeholder cert" openssl x509 -req -in fakecert.csr -signkey fakecert.key -days 1 -sha256 -out fakecert.crt
- Import the certificate into the truststore. If the
truststore.jksdoes not exist, thekeytoolwill create it.
keytool -importcert -file fakecert.crt -alias placeholder-cert -keystore truststore.jks
Enter keystore password: ENTER SOME PASSWORD HERE AND REMEMBER IT FOR LATER
Re-enter new password:
...
Trust this certificate? [no]: yes
Certificate was added to keystore
- Just some cleanup.
rm fakecert.key fakecert.csr fakecert.crt chmod 644 truststore.jks # the connector server user should not be able to write the truststore, only read it chown root:connector-server truststore.jks
- Add truststore to startup script
ConnectorServer.sh:
cd /opt/connector-server/connid-connector-server vim bin/ConnectorServer.sh # add this snippet to the command line that executes the connector server -Djavax.net.ssl.trustStore=/opt/connector-server/connid-connector-server/conf/truststore.jks -Djavax.net.ssl.trustStorePassword=PUT_KEYSTORE_PASSWORD_HERE
- Restart the connector server.
Remote connector server configuration - Windows
1) Install Java 1.8 (OpenJDK headless is preferred).
2) Unpack connector server to his root directory "C:\connid-connector-server".
3) Create trustore for connector server. Use git bash in direcotory "C:\connid-connector-server\conf".
- Get (or create - as we do there) a certificate of the end system.
openssl genrsa -out fakecert.key openssl req -new -key fakecert.key -out fakecert.csr -subj "/C=CZ/ST=Czech Republic/L=Prague/O=BCV/CN=Connector placeholder cert" openssl x509 -req -in fakecert.csr -signkey fakecert.key -days 1 -sha256 -out fakecert.crt
- Import the certificate into the truststore. If the truststore.jks does not exist, the keytool will create it.
/c/Program\ Files/Java/jdk-1.9.8/bin/keytool -importcert -file fakecert.crt -alias placeholder-cert -keystore truststore.jks
Enter keystore password: ENTER SOME PASSWORD HERE AND REMEMBER IT FOR LATER
Re-enter new password:
...
Trust this certificate? [no]: yes
Certificate was added to keystore
- Just some cleanup.
rm fakecert.key fakecert.csr fakecert.crt
4) Add trustore location and password to service installation in „bin\ConnectorServer.bat“(windows). These parameters are in script already, so just trustore path and password.
"-Djavax.net.ssl.trustStore=C:\connid-connector-server\conf\truststore.jks";"-Djavax.net.ssl.trustStorePassword=TODO_PASSWORD"
5) Start CMD under system admin. Then go to connector-server root directory.
cd C:\connid-connector-server bin\ConnectorServer.bat /setkey
6) Add connectors to "C:\connid-connector-server\bundles" and scripts to "C:\connid-connector-server\scripts".
7) Then setup connector-server key and install windows service(connector_server).
bin\ConnectorServer.bat /install connector_server
8) Then start service in "services.msc". If connector_server service started correctly set this service to automatic start.
Remote connector server agenda
@since 10.8.0
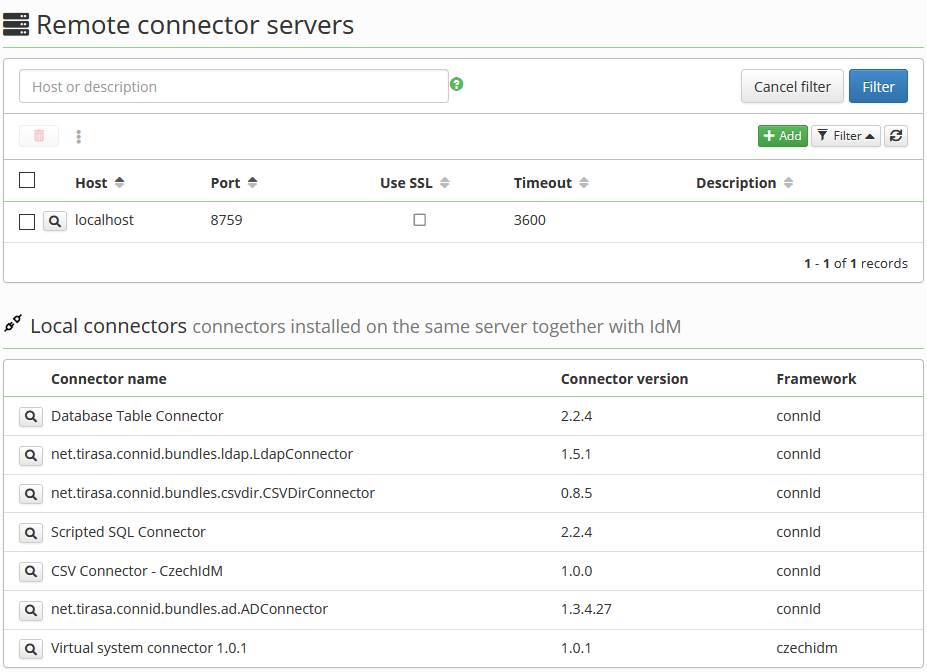
Standalone connector server agenda is available from main menu System → Connector servers:
- Remote connector servers can be configured here, configuration is effective for all related systems,
- connectors installed on the same server together with CzechIdM are shown,
- systems related to remote connector server or to concrete connector can be found on server or connector detail.
Connecting CzechIdM to a remote connector server
- In CzechIdM, go to
Systems→Connector serversfrom menu and add new remote connector server. - In the detail of this remote connector server fill in every form field that IdM needs to connect to the remote system. It is necessary to supply the host and port on which the connector is available on remote server. If the server is secured by password, you will need to fill in the password in order to successfully connect to the remote connector server. Password will be stored in local confidential storage.
- When you are done,
savethe form. - In CzechIdM, on the system tab, create a new system.
- In the detail of this system, select previously added remote connector server in
Use remote connector serverfield. - When you are done,
savethe form. - Go to the
Configurationstab. There, only connectors that are deployed inside remote connector server, will be available. - Configure everything else as you would do if you were not using remote connector server.
org.identityconnectors.framework.common.exceptions.InvalidCredentialException: Remote framework key is invalid