Roles
A role in CzechIdM is an entity representing a set (1 or many) of permissions/privileges on the end system or in CzechIdM itself. Users acquire roles:
- automatically – according to the organizational placement of the identity or identity attributes
- manually – through assigning based on the user’s request in the CzechIdM self-service or by a CzechIdM administrator.
From the perspective of the identity manager, it does not matter whether the user acquires an account in a specific application, is placed in a group in LDAP, his indication is set to “can use VPN”, or a permission is set for him in the application. In all the cases, a role is assigned. A simplification carried out like this allows general rules to be applied for assigning all types of permissions (~roles) in the same way.
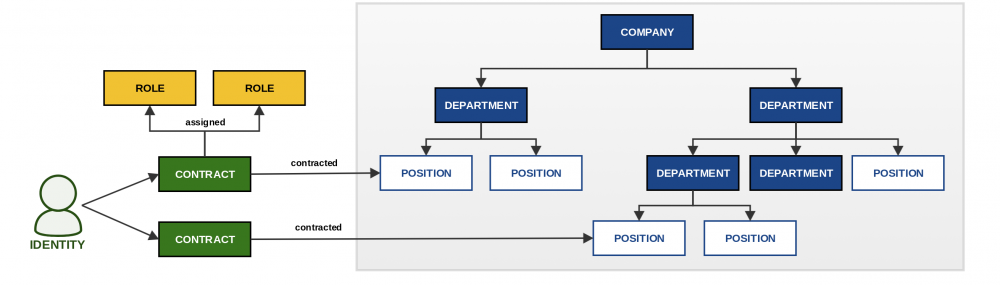
Roles and contracts
Roles are assigned to users via their contracts. If a contract is not valid (time validity) the roles on the contract are disabled. In other words, the role loses its permissions in IdM and rights in connected systems.
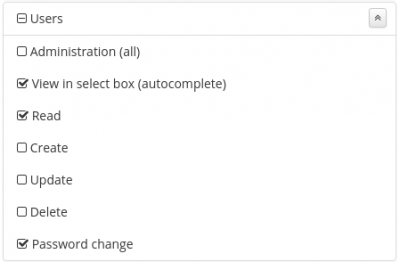
Role permissions
Role permissions define rights for administrator actions in CzechIdM. A permission for CzechIdM is not necessarily defined for every role. A permission is, for example, READ on USERS. A user having a role with this specific permission can see the read-only detail of all identities in CzechIdM.
Role criticality
The level of criticality can be set for every role. Criticality denotes, who approves its assignment. Role can have criticality from 0 to 5.
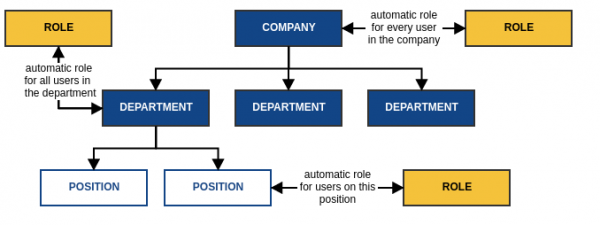
Automatically assigned roles by organization structure
The role can be linked to a Tree structure (e.g. position in organizational structure). That role is assigned to and removed from a user based on adding/removing the user (via their contract) to/from the organizational tree structure. If a contract is not valid yet, roles are assigned but are disabled until the contract starts.
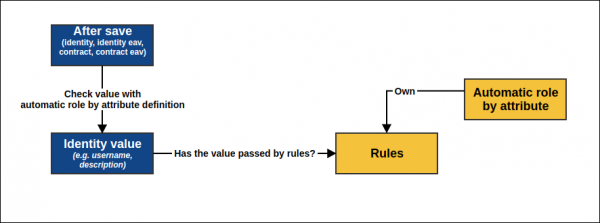
Automatically assigned roles by attribute
The role can be also linked with value in attribute (value can be stored in Identity, Identity extended attribute, Contract and Contract extended attribute). That role is assigned to and removed from a user based on the value in the specific attribute. Recalculating of this automatic roles is done after saving identity, identity extended attribute attributes, contract and contract extended attribute attributes. All necessary attributes that defined automatic role by attribute are defined by agenda "Automatic role by attribute".
Requests for change automatically assigned roles
Automatically assigned roles have a significant safety impact. When creating, editing, or deleting, it is necessary that the process is approved. For this purpose, an agenda for requests for change of automatic roles has been created.
This request gets the approval process from the criticality defined for that role. Critical role determines what process the application must accomplish to implement it.
Processes of defined by the role criticality is defined here. Processes for approval change of an automatic role are different then processes using for approving assign role to one user. For clarity, both processes (role assignment, change of the automatic role) are defined in one final process.